Securing any SaaS can be a confusing task, but using Exponential Backoff is a technique that even a CISO will love
When it comes to SaaS security, the landscape is a minefield of choices, trade-offs, and ever-evolving threats. Whether you’re a developer building your first authentication flow or a CISO overseeing thousands of users and endpoints, one principle remains true: simple techniques, when implemented smartly, can make a world of difference. One such technique? Exponential Backoff.
What Is Exponential Backoff?
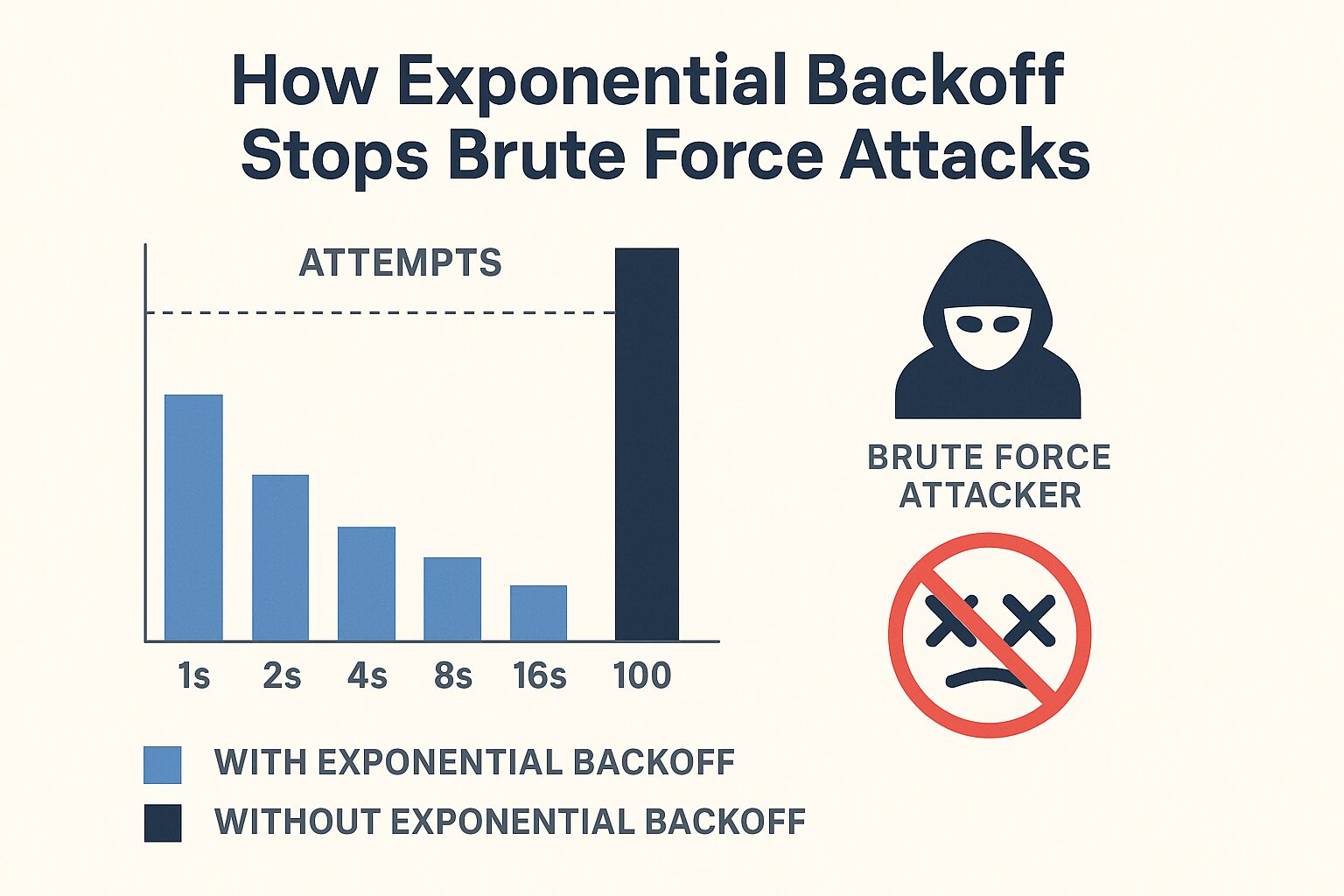
Exponential Backoff is a rate-limiting strategy that increases the wait time between repeated actions—usually failed login attempts or API requests—by a power of two. It starts with a short delay before a retry is allowed, then doubles it with each failure:
- 1st failure: 1 second until they can retry the login
- 2nd failure: 2 seconds
- 3rd failure: 4 seconds
- 4th failure: 8 seconds
This small tweak can have a massive impact on your application’s resilience to brute-force and credential stuffing attacks.
Why Attackers Hate It
Hackers thrive on speed and automation. Credential stuffing attacks, for example, rely on blasting login forms with thousands (or millions) of stolen usernames and passwords as fast as possible. If every failure doubles the wait time, their bots quickly become ineffective:
- Instead of trying 1,000 passwords in a minute, they might only get through 10, get frustrated, and give up.
- The computational and time cost skyrockets.
- The ROI drops. Significantly.
And that’s the point: you’re not making it impossible to attack, you’re making it not worth the effort.
Why CISOs Love It
CISOs are constantly balancing risk, user experience, and technical feasibility. Exponential Backoff checks all the right boxes:
- ✅ Security: It acts as a force multiplier for your existing auth mechanisms.
- ✅ Scalability: It’s algorithmic, easy to implement, and lightweight.
- ✅ User experience: Unlike CAPTCHAs or aggressive account locks, it doesn’t frustrate legitimate users after one or two honest mistakes.
- ✅ Observability: It provides clear telemetry on potential attack patterns (e.g., repeated failures from the same IP).
Real-World Implementation Tips
- Cap the maximum delay – Don’t let backoff times stretch into absurdity. After, say, 5 failures, max out at a 1–2 minute delay.
- Use jitter – Add randomness to the delay time to prevent attackers from predicting exact intervals.
- Tie it to both IP and account – Prevent a distributed attack from bypassing delays by rotating IPs.
- Combine with alerts – Trigger alerts after a certain threshold to detect potential credential stuffing or targeted attacks.
Final Thoughts
In a SaaS world overloaded with zero-days, APIs, and compliance requirements, Exponential Backoff is one of those elegant techniques that delivers real security value with minimal complexity. It won’t solve every problem, but it will slow attackers to a crawl and give your security team the visibility and breathing room they need.
And for once, that’s something even a CISO can smile about.


Leave a Reply